本文最后更新于 2024年8月23日 下午
frp 是一个专注于内网穿透的高性能的反向代理应用,支持 TCP、UDP、HTTP、HTTPS 等多种协议,且支持 P2P 通信。可以将内网服务以安全、便捷的方式通过具有公网 IP 节点的中转暴露到公网。
下载地址:https://github.com/fatedier/frp
1、frp 服务端配置
提示:在安全组策略放通对应的端口
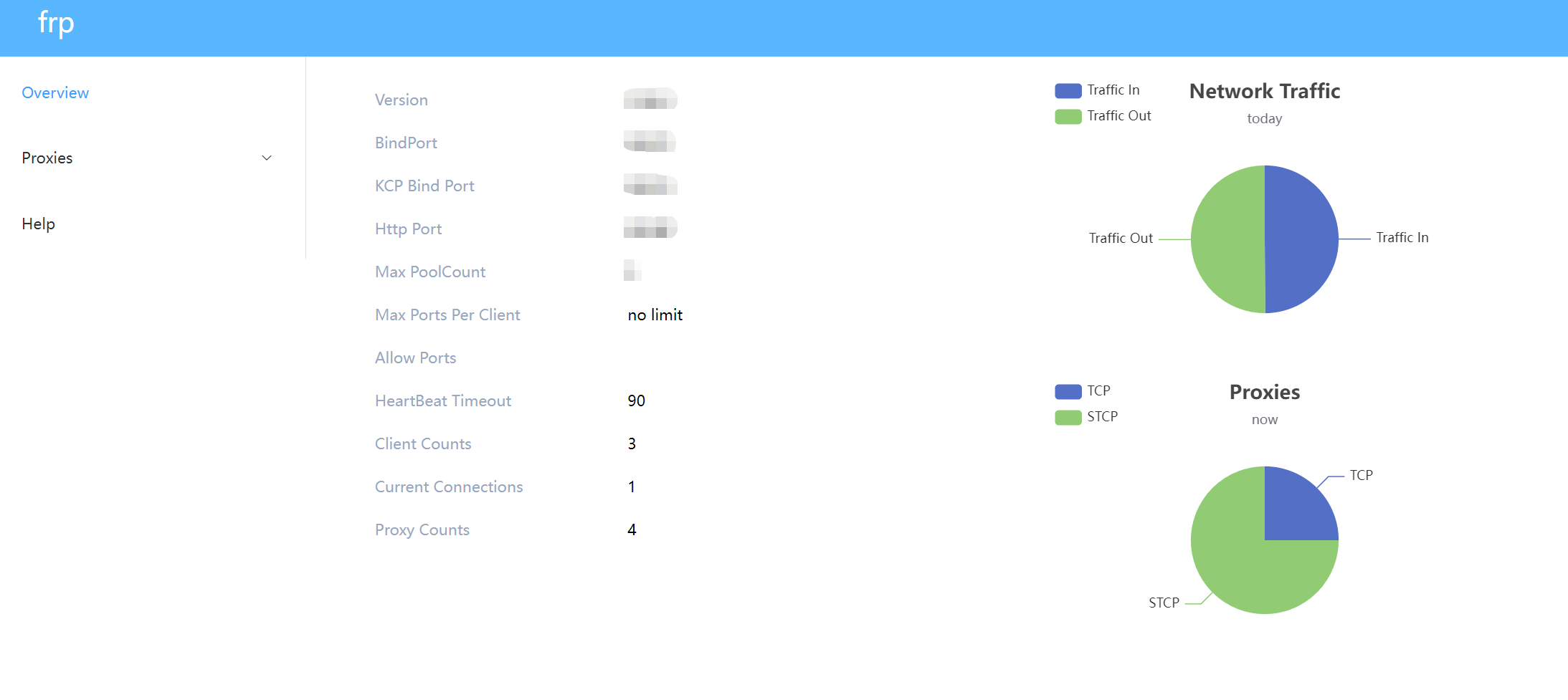
frp服务端配置文件:frps.ini
1
2
3
4
5
6
7
8
9
10
11
12
13
|
[common]
bind_addr = 0.0.0.0
bind_port = 501
kcp_bind_port = 501
bind_udp_port = 502
vhost_http_port = 580
token = 123456
dashboard_port = 500
dashboard_user = frp
dashboard_pwd = 123456
|
运行frps:nohup ./frps -c ./frps.ini >/dev/null 2>&1 &
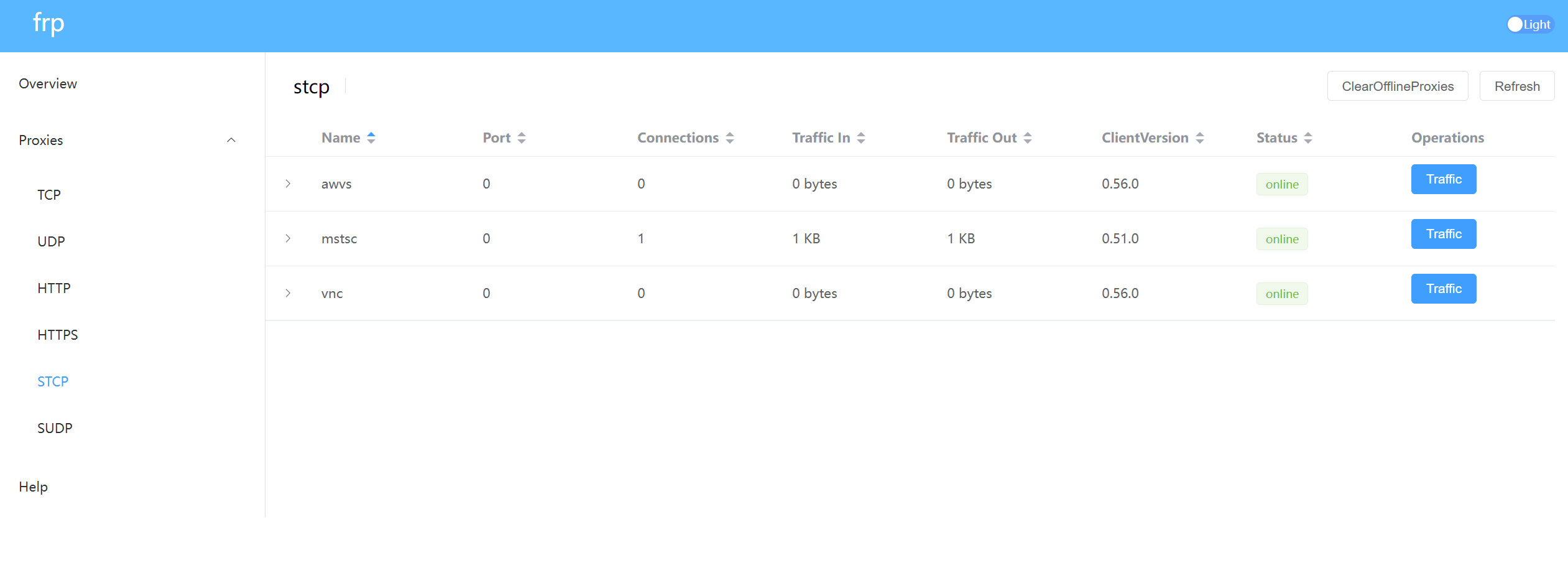
2、P2P 端口映射
主机A - 被访问端
修改配置文件:frpc.ini
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| [common]
server_addr = vps ip
server_port = 501
token = 123456
[mstsc]
type = stcp
sk = 123456
local_ip = 127.0.0.1
local_port = 3389
[vnc]
type = stcp
sk = 123456
local_ip = 127.0.0.1
local_port = 5900
[awvs]
type = stcp
local_ip = 127.0.0.1
local_port = 13443
[socks5]
type = tcp
remote_port = 510
plugin = socks5
plugin_user = root
plugin_passwd = 123456
|
运行:frpc.exe -c frpc.ini
主机B - 访问端
修改配置文件:frpc.ini
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| [common]
server_addr = vps ip
server_port = 501
token = 123456
[mstsc]
type = stcp
role = visitor
server_name = mstsc
sk = 123456
bind_addr = 127.0.0.1
bind_port = 3390
[vnc]
type = stcp
role = visitor
server_name = vnc
sk = 123456
bind_addr = 127.0.0.1
bind_port = 5900
[awvs]
type = stcp
role = visitor
server_name = awvs
bind_addr = 127.0.0.1
bind_port = 13443
|
运行:frpc.exe -c frpc.ini
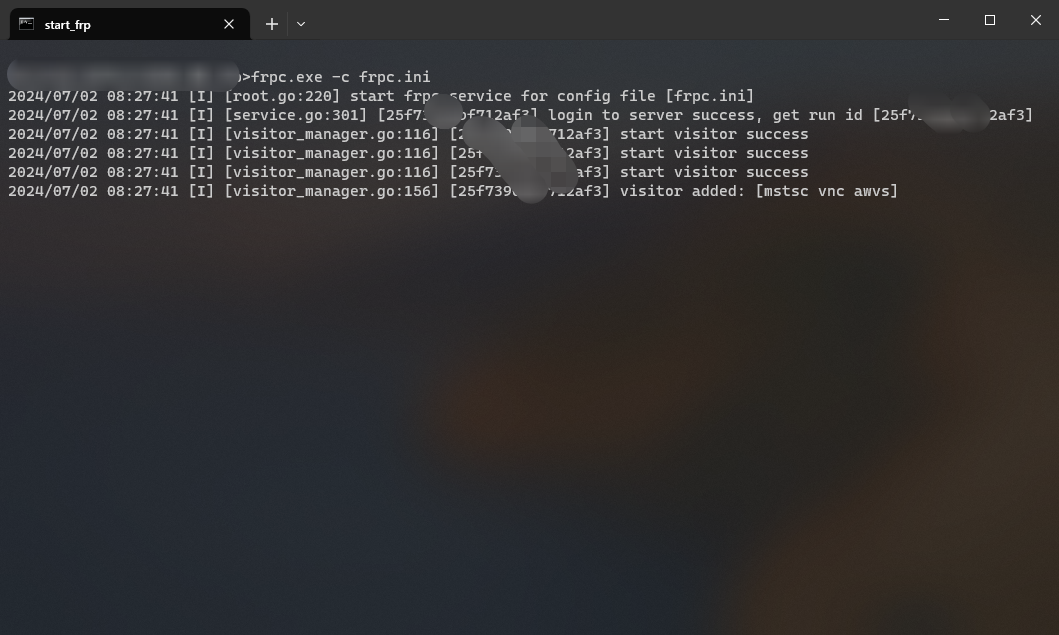
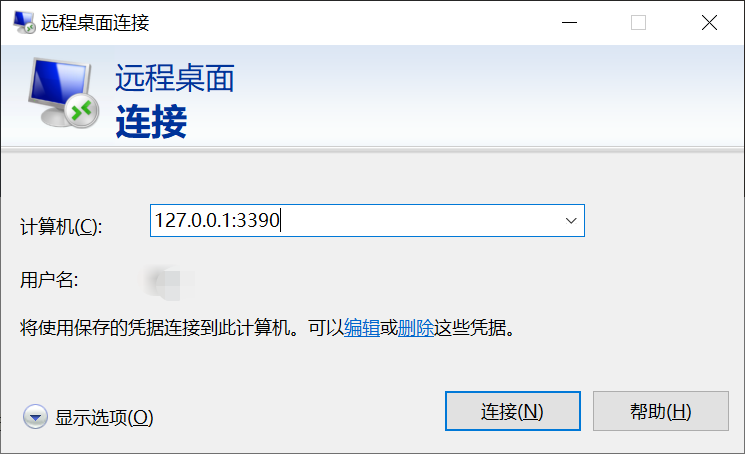
主机B 远程桌面 主机A
- 运行:
frpc.exe -c frpc.ini
- 主机B
3390端口 绑定 主机A3389端口
- 远程桌面地址:
127.0.0.1:3390
3、搭建 socks5 隧道
- 修改客户端配置文件:
frpc.ini,使用代理后,流量通过客户端的网络进行访问。
- 代理地址:
socks5://vps_ip:510
- 认证信息:
root/123456
1
2
3
4
5
6
7
8
9
10
11
| [common]
server_addr = vps ip
server_port = 501
token = 123456
[socks5]
type = tcp
remote_port = 510
plugin = socks5
plugin_user = root
plugin_passwd = 123456
|
运行:frpc.exe -c frpc.ini



